
News, Insights, and more on Industrial IoT

Over the past decade, highly publicized cybersecurity breaches have revealed weaknesses in our prevailing IT security models.
In 2013, Edward Snowden took 20,000 documents from the NSA without using any sophisticated devices or software. In the same year, hackers stole credit and debit card data from 40 million Target customers by exploiting a vulnerability in the retailer’s building management system.
Sony also dealt with a large-scale security breach when hackers erased sensitive documents, unreleased media, and private information, taking advantage of the company’s poor data management practices. Two security researchers from Twitter and IOActive even proved they could hack into a moving automobile and control critical systems. That was five years ago.
Tying all of these situations together is a common thread: infrastructure and systems were secure, but the information within them was not. In each case, hackers tore through external security infrastructure and gained access to unprotected data. Once they bypassed whatever IT protections were in place, they could do whatever they wanted.
Up until now, the cybersecurity industry has focused on “perimeter-centric” security. Under this approach, companies build digital fences and moats around their data to keep bad actors out without securing the assets on the inside. So, the containers that hold information are protected, but the information itself is not (think: defenseless villagers inside a well-guarded castle).
 Perimeter-centric security models try to keep sensitive information behind a firewall.
Perimeter-centric security models try to keep sensitive information behind a firewall.
Perimeter-centric security works for smaller systems and those isolated from the internet. However, once you go online, things start to break down.
In the modern world, data is no longer confined within well-defined digital perimeters. Remote work is dramatically expanding the digital footprints that IT security teams have to protect. COVID-19 is accelerating this transition, forcing many to reconsider cybersecurity practices earlier than anticipated. On top of that, the Internet of Things (IoT) is pushing actual IT infrastructure out to the edge.
A patchwork of systems has helped keep perimeter-centric security models afloat. Between anti-virus applications, data loss prevention (DLP) software, and other legacy security protocols, we’ve managed to keep the ship from sinking. However, these solutions are no longer suited for modern cybersecurity needs. They only perpetuate a false sense of security that leaves organizations vulnerable over the long run.
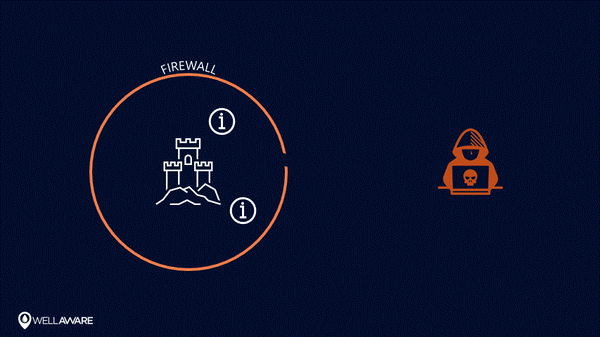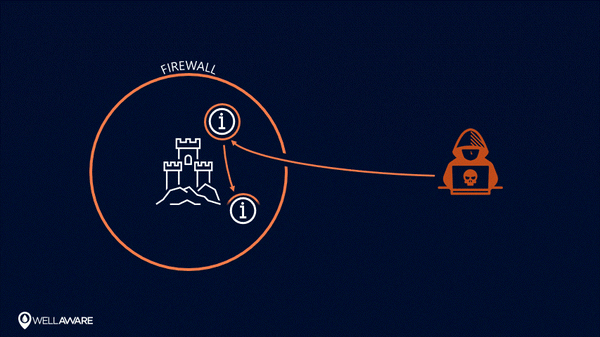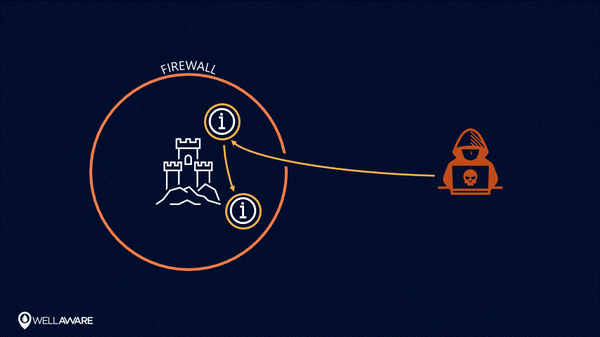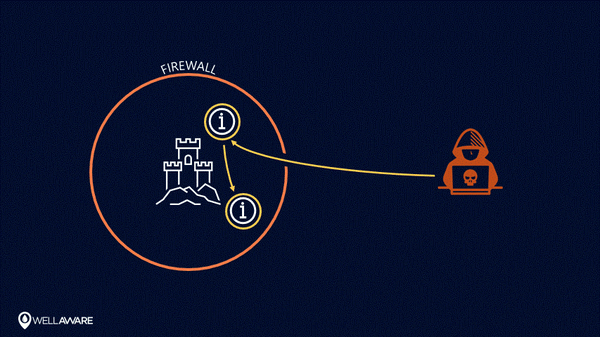 Once breached, perimeter-centric security models are useless at protecting information.
Once breached, perimeter-centric security models are useless at protecting information.
According to a report from Lloyd’s Register Foundation, industrial IoT (IIoT) security has reached a tipping point. IIoT environments and devices are getting deployed faster than operational security capabilities are evolving. We are falling behind fast.
Over a decade ago, Carnegie Mellon urged US leaders to start transitioning to information-centric security models. Today, we still think this is the best path to IIoT security success. We’ll take it even one step further: we need information-centric and infrastructure-centric security. The best solutions going forward will be those that protect individual data and assets rather than further bolster failing perimeters.
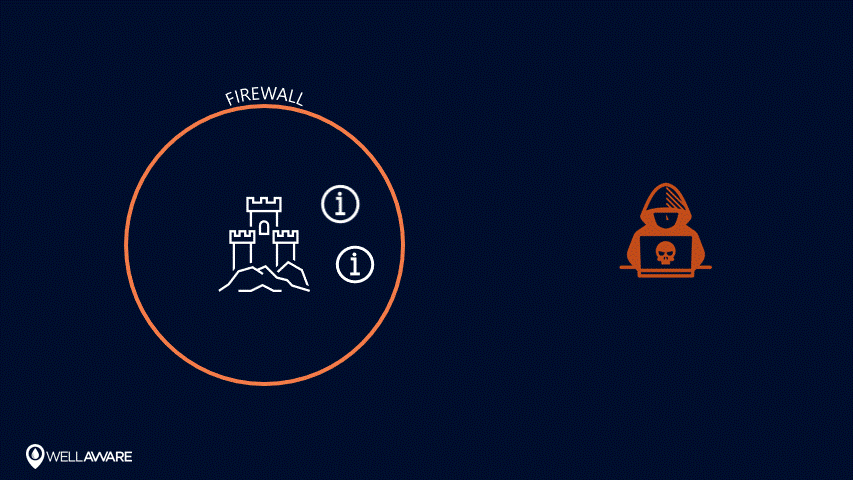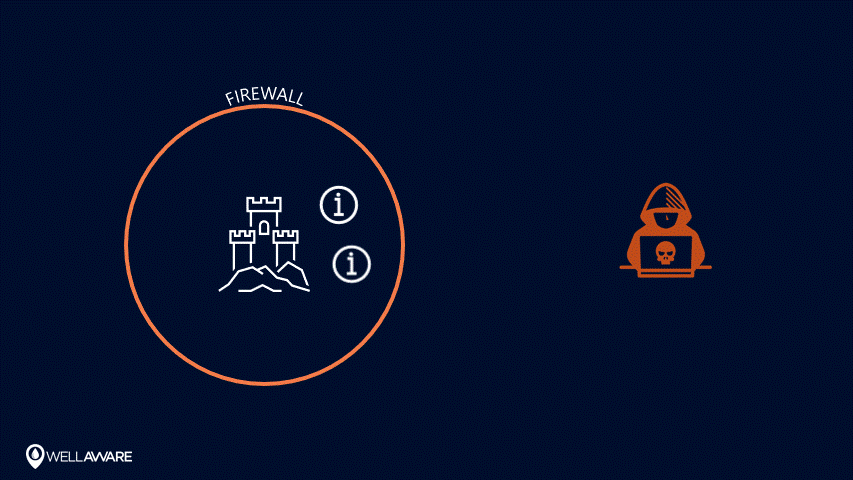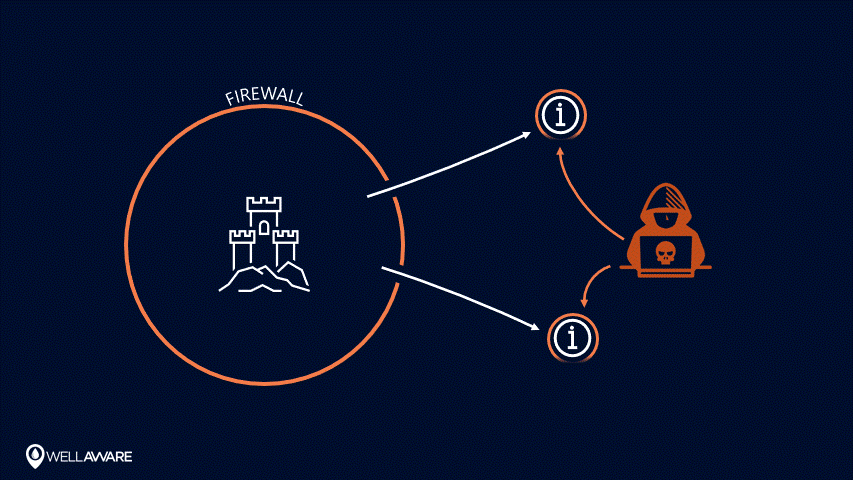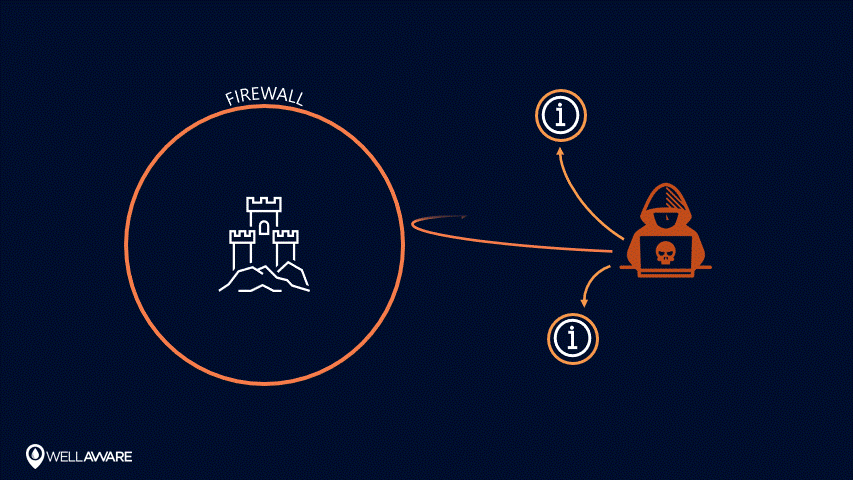 With perimeter-centric security, information outside of the perimeter is no longer safe.
With perimeter-centric security, information outside of the perimeter is no longer safe.
Information-centric focuses on inherently securing the sensitive information that hackers like to access. In its simplest form, information-centric security could look like encrypting individual files with passwords. No matter where files go, they always require user authentication to access. Under the information-centric security model, if password-protected assets are stolen or maliciously accessed, they are still safe.
Of course, the challenge with this approach is that encrypting every piece of information manually is impossible for users and security managers. No organization has a password management app powerful enough to handle such volume.
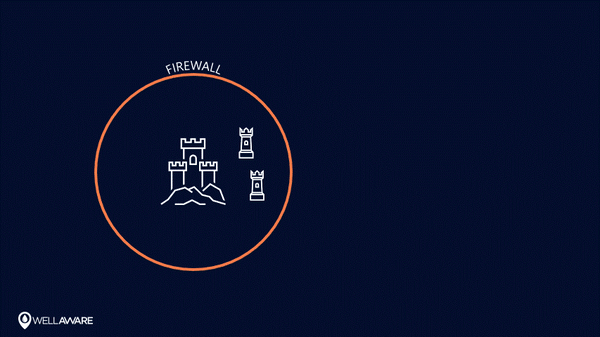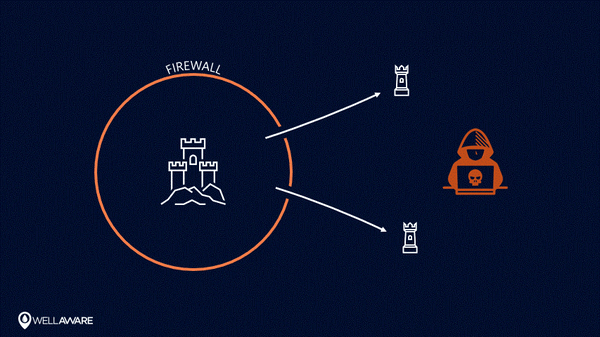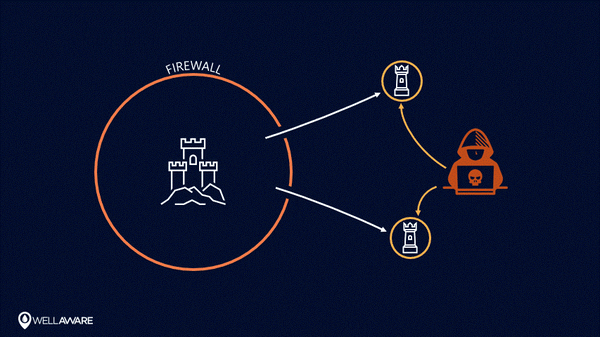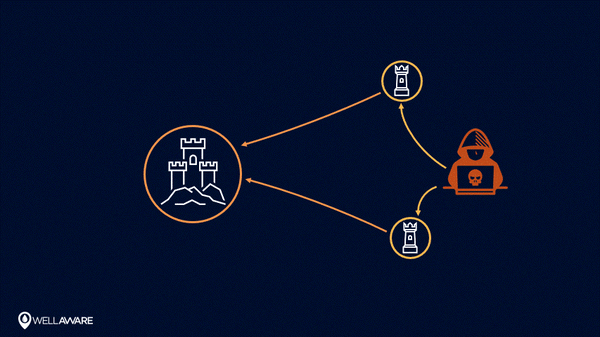 Using perimeter-centric security models in the IoT - when infrastructure leaves the perimeter - can put the whole system at risk
Using perimeter-centric security models in the IoT - when infrastructure leaves the perimeter - can put the whole system at risk
At WellAware, we believe modern organizations need security solutions that are based on identity and permissions, not on keys and passwords. If you have clearance and can confirm who you are, then you should be able to access what you need. This factors in a key tenant of information-centric security: keeping business context top of mind.
To do this for the IoT and beyond, the encryption process must be completely transparent. With billions of devices flooding the market every year, we don’t have time to manually encrypt every IoT device. Companies need IoT security frameworks with inherent encryption mechanisms that enable users to extend permissions based on identity.
Consider the following example:
Bob encrypts a document with his favorite password (“ABC”) and gives coworker Alice permission to read and write the document. Under a typical information-centric security model, Bob would have to share his password with Alice. Obviously, this isn’t a sustainable or reasonable solution, especially if you treat “Bob” and “Alice” as independent IoT devices.
A better approach would involve shifting the password protection mechanism away from the document itself and tying access to the users themselves. Bob could give Alice read and write permission over a document that she would access using her unique identity “key.” Alice could use her own password (“XYZ”), and Bob wouldn’t have to share his. In fact, Bob wouldn’t even have to remember his password for Alice to retain access.
 Zero-trust networks are one way to add information-centric and infrastructure-centric concepts to your security policies.
Zero-trust networks are one way to add information-centric and infrastructure-centric concepts to your security policies.
When discussing IIoT security solutions, the identity keys approach is especially useful as Things have unique identities as well. Rather than manage enormous password libraries, IT security workers would simply have to set permissions according to unique user and Thing identities.
Today, we need scalable solutions like this that offer information security for any data type, make life easier for users, and integrate seamlessly with existing infrastructure.
At WellAware, we build solutions like this.
We recognize that the world is becoming more and more connected every day, so we’ve designed our security platforms accordingly. In our hyper-connected world, we allow information owners to protect data no matter where it resides and extend permissions as needed. We enable organizations to effectively balance security and productivity, which has been a significant challenge over the last several years.
 Sign up for our Cybersecurity Webinar on August 13th!
Sign up for our Cybersecurity Webinar on August 13th!
To learn more about how WellAware ensures IIoT deployments are safe and secure, contact us today.
Like what you're reading? Sign up for updates!
Have a Question?